4 Proven Ways to Mitigate the Costs of Data Theft

No business wants to experience data breaches. Unfortunately, these days, it's difficult to completely avoid them. Approximately 83% of organizations have experienced more than one data breach. (IBM Security 2022 Cost of Data Breach Report )
These breaches harm businesses in several ways. First, there is the immediate cost of remediating the leak. Then there are the costs of lost productivity. Add to this the loss of business contracts and loss of customer trust. A business could also incur significant legal costs associated with a breach.
According to the IBM Security report, the cost of a data breach has increased again in 2022. The global cost of a breach is now $4.35 million, up 2.6% from last year. If your company is in the United States, the cost rises to $9.44 million. In Canada, the average data breach costs companies $5.64 million.
Costs for small businesses tend to be slightly lower, but breaches are often more devastating for SMEs. They don't have the same resources as larger companies to offset all these costs.
It is estimated that 60% of small businesses fail within six months of a security breach.
Businesses don't need to resign themselves to the impending disaster of a data breach. There are proven tactics that can be adopted to mitigate costs. These cybersecurity practices can limit the damage of a cyberattack. Learn more about essential security practices, preparing for cyberattacks, and IT succession planning.
All of these findings come from the IBM Security report, which includes concrete facts about the benefits of strengthening your cybersecurity strategy.
Cybersecurity tactics to reduce the impact of a data breach
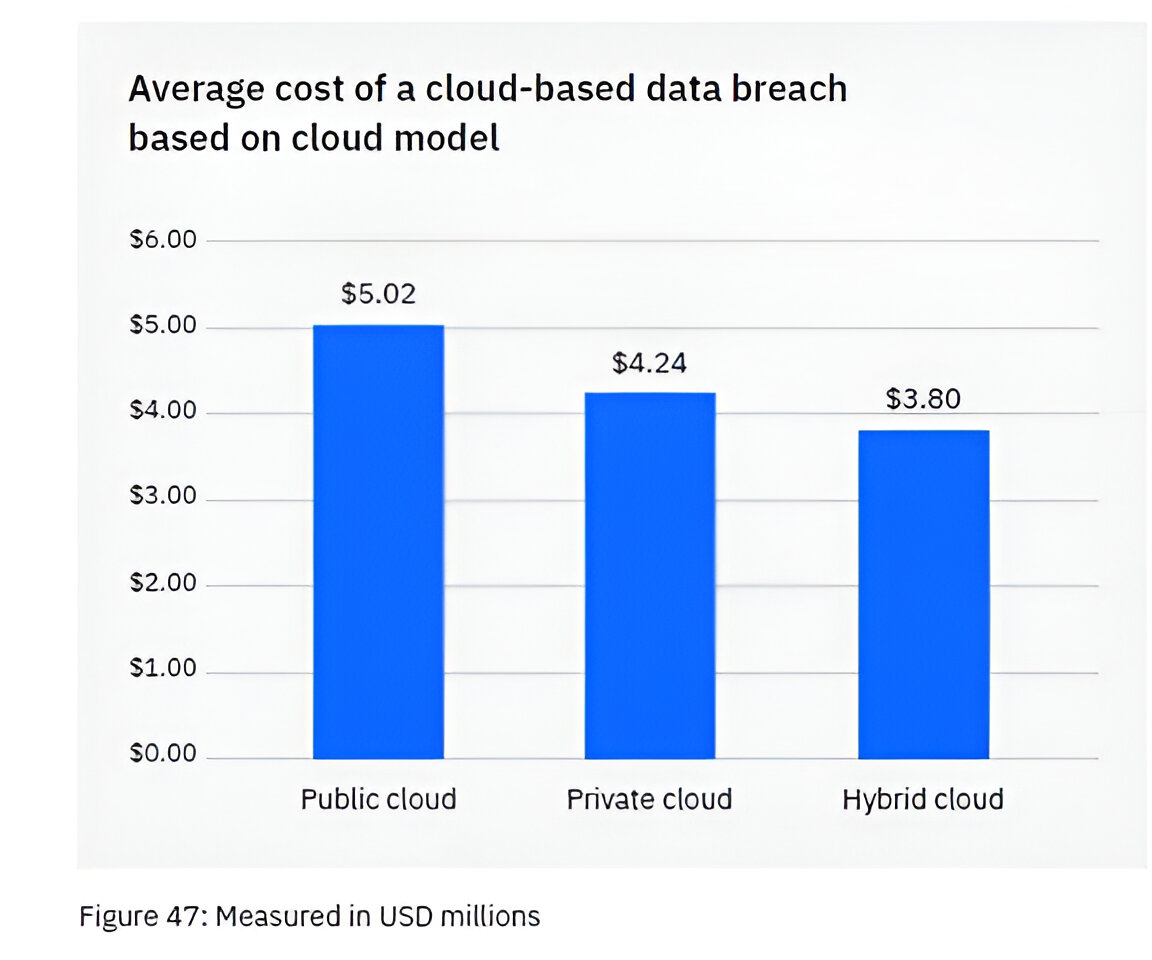
Use a hybrid cloud approach
Most organizations use the cloud for data storage and business processes. Researchers have found that 45% of all data breaches occur in the cloud, but not all cloud strategies are created equal.
Breaches in the public cloud are much more costly than those in a hybrid cloud. What is a hybrid cloud? It means that some data and processes reside in a public cloud, while others reside in a private cloud environment.
What some may find surprising is that using a hybrid cloud approach was also better than a private cloud.
Implement and practice an incident response plan
You don't need to be a large company to create an incident response (IR) plan. An IR plan is simply a set of instructions that employees must follow if a certain number of cybersecurity incidents occur. Here's an example: in the case of ransomware (malware), the first step is to disconnect the infected device. IR plans improve the speed and effectiveness of a response to a security crisis. Having a practical incident response plan reduces the cost of a data breach by an average of $ 2.66 million per incident.
Adopt a Zero Trust security approach
A Zero Trust approach is a set of security protocols that work together to strengthen a network. For example:
- Multi-factor authentication
- Safelisting of applications
- Contextual user authentication
Approximately 79% of critical infrastructure organizations have not adopted a Zero Trust approach. This can significantly reduce data breach costs. Organizations that do not deploy Zero Trust tactics pay approximately $1 million more per data breach.
Use AI security tools and automations
Using the right security tools can make a big difference in the costs incurred during a data breach. Using tools that deploy security AI and automation has led to greater savings.
Data breach spending has decreased by 65.2% thanks to security AI and automation solutions. These types of solutions include tools such as Advanced Threat Protection (ATP). They can also include applications that track threats and automate response. For foundational protection, review endpoint security and choosing the right firewall.
How to start improving your cyber resilience
Many of these ways to reduce the costs of data breaches are simply best practices. You can begin incorporating them one by one by rolling out upgrades to your cybersecurity strategy.
Work with a trusted IT provider to establish a roadmap. Address the low-hanging fruit first. Then move on to longer-term projects.
For example, a "low-hanging fruit" would be implementing multi-factor authentication. This is inexpensive and easy to implement. It also significantly reduces the risk of a cloud breach.
A long-term project might be creating an incident response plan. Then, you'll set a schedule for your team to regularly practice the plan. During these exercises, you can troubleshoot any issues.
Need help improving your security and reducing risks?
Working with a trusted IT partner relieves you of much of the security burden. Contact us now to schedule a conversation about a cybersecurity roadmap. Learn how to choose the right managed IT service provider.
About Nexxo
Nexxo Computer Solutions specializes in providing IT and technology services to Quebec businesses. Its mission is to offer Quebec companies IT services tailored to their needs. Acting as an external IT department, it handles all of a company's IT tasks, allowing it to focus on its business activities. It achieves this by collaborating closely with its clients and putting their interests at the center of its concerns.
Stay Ahead with Expert Insights
Subscribe to our newsletter for the latest tips and updates in the tech industry.

.svg)